
Comprehensive Information Security Services
Protect your digital future with CloudSynergi's end-to-end information security solutions. In an era of evolving cyber threats, leveraging specialized expertise is not just an option—it's a business imperative. We provide the strategic and technical services you need to build a resilient security posture, manage risk, and foster trust, allowing you to focus on your core business objectives
Cloud Security & SECaaS (Security as a Service)
Operate confidently in the cloud with solutions designed for modern environments. Our services include Cloud Security Posture Management (CSPM) to find and fix misconfigurations, Cloud Workload Protection (CWPP) for your servers and containers, and data security for your cloud storage. We help you implement a secure-by-design cloud architecture.
AI-Powered Security & Threat Management
Turn the tide on cyber adversaries with artificial intelligence. We deploy AI-driven tools for advanced threat detection, behavioral analytics, and automated incident response. This allows for faster identification of malware, anomalies, and sophisticated attacks that traditional tools might miss, shifting your operations from reactive to proactive.


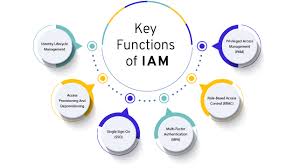
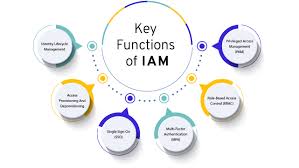
Identity and Access Management (IAM) & Zero Trust
Secure your new perimeter: identity. With hybrid work and cloud applications, managing who has access to what is critical. We help you implement Zero Trust architectures and robust IAM solutions, enforcing the principle of least privilege and ensuring that only authorized users and devices can access your sensitive resources.
Data Protection & Privacy
Safeguard your most valuable asset—your data. Our comprehensive data protection services include data classification, encryption, Data Loss Prevention (DLP), and data masking. We ensure you maintain compliance with global regulations like GDPR, HIPAA, and PCI DSS, protecting you from both external breaches and internal threats.
Managed Security Services (MSSP) & 24/7 Monitoring
Bridge the cybersecurity skills gap and gain continuous protection. Our Managed Security Services provide round-the-clock monitoring, threat hunting, and incident response from our dedicated Security Operations Center (SOC). This gives you access to expert skills and advanced tools without the overhead of building an in-house team.






Compliance, Risk Management & Cyber Resilience
Navigate the complex regulatory landscape with confidence. We offer services in security program development, risk quantification, and compliance management. Our experts help you build cyber resilience—preparing for, responding to, and recovering from security incidents to ensure your business continuity.

2025 Information Security Trends: What You Need to Know
The AI Revolution: AI is a double-edged sword. While security teams use it for automation and threat detection, attackers use it to create more sophisticated malware and hyper-realistic phishing campaigns. Managing "Shadow AI" within your organization has become a top priority.
The Rise of Identity as the New Perimeter: The traditional network perimeter is gone. Zero Trust architectures, which verify every access request as if it comes from an untrusted network, are becoming the standard. This focuses security on identity and access management.
The Shift to Platform Consolidation: Organizations are moving away from fragmented security tools. There is a strong trend towards platform aggregation and integrated solutions like CNAPP (Cloud-Native Application Protection Platform) and XDR (Extended Detection and Response) for unified visibility and control.
The Growth of SECaaS and Managed Services: The Security as a Service (SECaaS) market is booming, projected to reach $23.8 billion by 2026. Companies are leveraging MSSPs to access expertise, achieve 24/7 monitoring, and manage costs effectively.
Quantum Preparedness Begins: While still emerging, the threat quantum computing poses to current encryption is real. Forward-thinking organizations are now beginning to plan for the transition to post-quantum cryptography to future-proof their sensitive data.
Why Partner with CloudSynergi?
Expertise on Demand: Gain immediate access to seasoned security professionals with diverse specializations, overcoming the industry-wide talent shortage.
Cost-Effective & Scalable: Achieve enterprise-grade security with a predictable subscription model. Our services scale with your business, avoiding large upfront investments in hardware and personnel.
Proactive & Continuous Protection: Move beyond reactive measures. Our 24/7 monitoring and threat hunting capabilities ensure that threats are identified and neutralized swiftly, minimizing potential impact.
Focus on Your Business: Delegate the complexity of security management to us. Free up your internal IT team to focus on strategic initiatives that drive growth and innovation.




